We know, as NDIS providers, you're quite busy focusing on the thing that matters most: providing quality support to participants. However, the rise of digital tools has also meant an increase in cyber threats. We've all seen the headlines. Data breaches and cyber-attacks are not a distant threat, they are a reality for many businesses, big and small, including NDIS providers.
Why is this so important for NDIS providers?
According to the Office of the Australian Information Commissioner Notifiable Data Breaches Report (July - Dec 2024), health service providers (including disability services) reported the highest number of breaches or attacks across all industries.
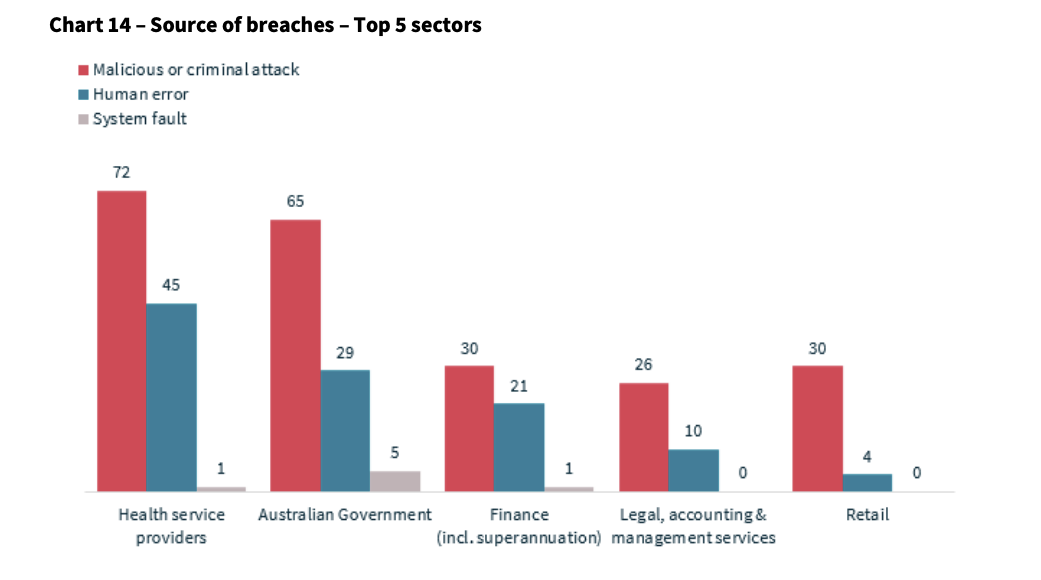
And the data you hold isn't just any data. It's deeply personal and sensitive information about the people you support, including:
- Participant records: Assessment, plans, and case notes.
- Financial information: Billing details, NDIS plan funding and bank accounts.
- Personal details: Addresses, contacts and private notes.
This information is gold for cybercriminals. It also means a breach isn't just a technical glitch, it's also a direct risk to the safety and privacy of the people you support. And it’s a breach of trust that can cause long-term reputational damage.
Compliance also isn’t optional. Like all Australian businesses, NDIS providers have legal and ethical obligations under the Privacy Act 1988 and the Cyber Security Act 2024 to protect participant data and need to be able to demonstrate their compliance.
What do cyberattacks look like in the disability sector?
Cyberattacks come in many forms, with some common ones including:
- Phishing scams: fraudulent emails, text messages or websites that try to trick people into revealing sensitive information like passwords or bank details. Sometimes these get pretty clever and use publicly available data to generate emails that look like legit requests from a user’s manager.
- Data breaches: when a third-party system is hacked. For example, in 2022, the CTARS data breach exposed sensitive medical and personal information of NDIS participants when the cloud-based application, which was used by NDIS providers, was hacked (Read more: Choice).
- Ransomware: hackers hold your data hostage, locking everything and demanding you pay a fee for it to be released. They may threaten to publish sensitive records if a ransom isn’t paid. Beyond the financial and reputational risks, service delivery is also impacted when providers are left unable to access essential files or software. In 2023, legal firm HWL Ebsworth, which handled NDIS-related matters, was targeted in a massive ransomware attack putting participant information at risk. (Read more: ABC).
What the heck can I do about it?
We know that cybersecurity can sound daunting, technical and maybe even a little boring. But it doesn't have to be. Think of it less as a complex IT project and more as an extension of your commitment to privacy and delivering a quality service.
The good news is that you don’t need to be an expert to make a difference. Here’s where to start:
- Know your risks. Every organisation is different. A risk assessment can help you identify your most valuable data and the biggest threats to it.
- Start with the basics:
- Strong passwords: This is your first line of defence. Use strong, unique passwords for all your accounts. (Yes, all of them!)
- Multi-Factor Authentication (MFA): For an extra layer of protection, turn on MFA wherever possible so even if your password is compromised, hackers cannot get access to your accounts.
- Regularly update your software. This might seem tedious, but it's crucial. Hackers often exploit vulnerabilities in outdated software. Keep your operating systems, apps and devices up-to-date.

- Strong passwords: This is your first line of defence. Use strong, unique passwords for all your accounts. (Yes, all of them!)
- Have a plan. What would you do if you (or your business) was attacked tomorrow? How would you respond to a ransomware attack? How would you notify participants of a data breach?
- Educate yourself and your team. Human error is a leading cause of breaches. Staff need to be able to recognise scams, suspicious links and unusual requests. Tech alone won’t save you. Well trained staff are your strongest defence.
By taking these practical steps, you can protect your business and continue upholding the trust that your participants and their families place in you every single day.
:format(jpg))

